Reverse engineering
I like to take things apart to figure out how they work, document their functions and build new, interoperable things. Here are some of the highlights of my reverse engineering projects. For all of them, see Category:Reverse engineering.
Talks
The Joy of Taking Things Apart
 This is an annotated transcript of a talk I gave at HackRice about reverse engineering and some of the fun projects/hacks they could do with reverse engineering skills. Some of the results were reported in the news. Read on for the presentation...
This is an annotated transcript of a talk I gave at HackRice about reverse engineering and some of the fun projects/hacks they could do with reverse engineering skills. Some of the results were reported in the news. Read on for the presentation...
Reverse Engineering with Hopper
 |
 |
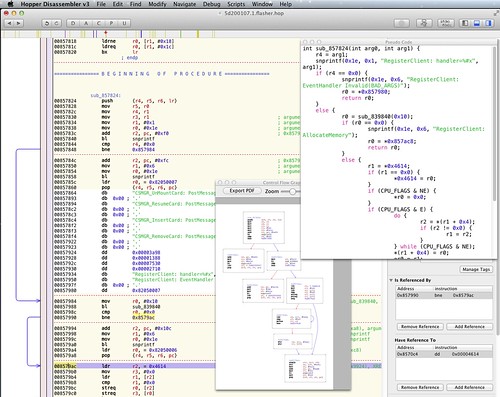
I taught an intro to reverse engineering with Hopper class at NYC Resistor. Hopper is a full featured interactive disassembler for i386, x86-64 and ARM CPUs, with a "decompiler" that generates mostly readable pseudo-code. Slides and example binary to disassemble.
Firmware
Magic Lantern firmware
 |
 |
| Original logo | Focus peaking on the LCD |
In 2009 I reverse engineered the firmware in the Canon 5D Mark 2 camera and wrote the Magic Lantern firmware to add features that I needed for some of my film projects. Since then it has been ported to nearly every Canon DSLR model and provides an enormous range of features including RAW video and HDR. It even has a wikipedia page. Read on for more details...
Mac EFI firmware
 Thunderstrike is the name for a class of Apple EFI firmware security vulnerabilities that allow malicious software or Thunderbolt devices to flash untrusted code to the boot ROM and propagate via shared devices. It was presented at 31C3. Read on for more info on Thunderstrike or Thunderstrike 2, a software-only extension.
Thunderstrike is the name for a class of Apple EFI firmware security vulnerabilities that allow malicious software or Thunderbolt devices to flash untrusted code to the boot ROM and propagate via shared devices. It was presented at 31C3. Read on for more info on Thunderstrike or Thunderstrike 2, a software-only extension.
ROMs
 |
 |
Old ROMs frequently hold hidden secrets (like the Mac-SE Easter Egg images) and modern ROMs often have security issues to be analyzed. I've designed PROMdate, a reader built with the Teensy++ for up to 40 pin DIP chips that can handle most common +5V ROM/PROM/EPROM/EEPROM/etc chips, and an 8 pin SOIC clip reader for SPI flash ROMs. Read on for more ROMs...
List of pages
- Airbreak.dev: Jailbreak for CPAP machines
- C64 font
- DMCA 1201 exemption panel discussion
- Epilog driver
- FT 817
- Fuji X100
- Hebrew font
- Ikea
- Inverse kinematics
- Mac SE Easter Egg
- Mac
- Magic Lantern firmware
- Muybridge ROM
- Pager
- PROMdate
- Reverse engineering class
- Reverse engineering with Hopper
- Robot arms
- ROM
- safeboot: Booting Linux more safely
- SPI flash
- Taking things apart
- Thunderstrike 2 media
- Thunderstrike 2
- Thunderstrike at 31C3
- Thunderstrike2 demo
- Thunderstrike2 details
- Thunderstrike
- Voyager
- VZL file
SPI Flash reader
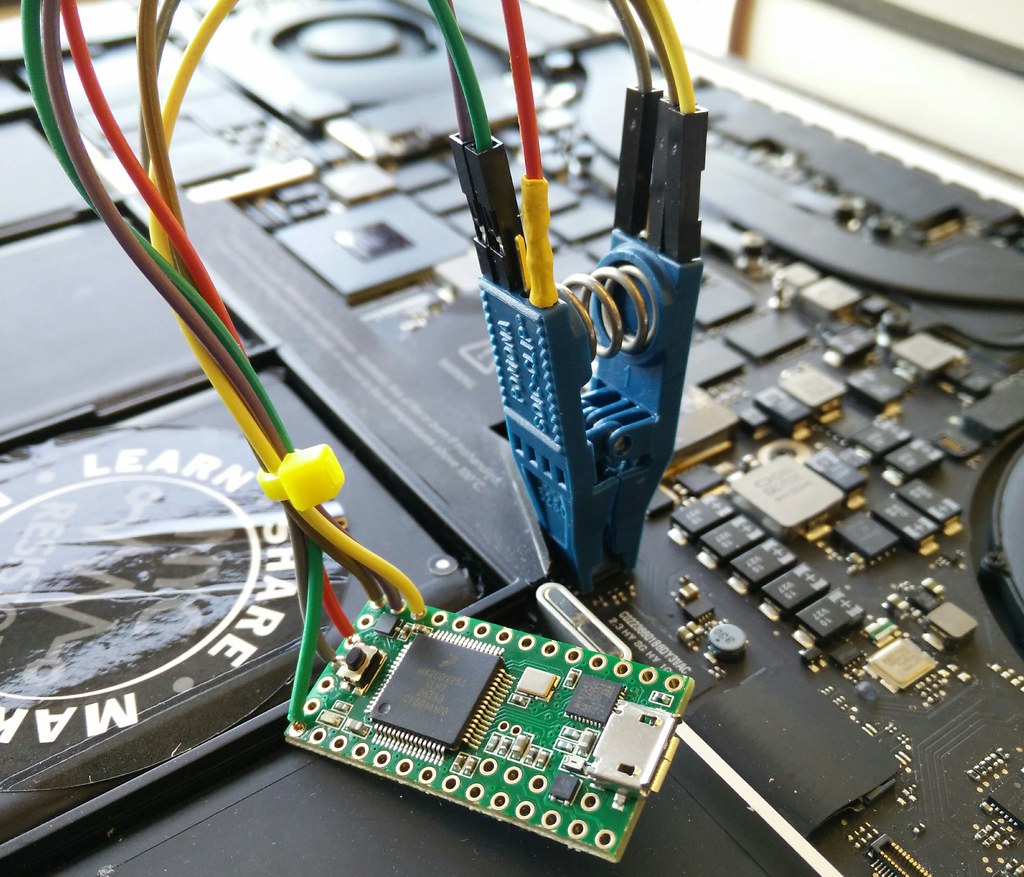 Like ho.ax, I had been using a Dangerous Prototypes buspirate to read SPI flash boot ROMs, but it was too slow. So I built a dedicated one with a Teensy 2 or 3 and a 8-SOIC chip-clip. It can read/write the entire multi-megabit ROM in a minute. Read on for more info...
Like ho.ax, I had been using a Dangerous Prototypes buspirate to read SPI flash boot ROMs, but it was too slow. So I built a dedicated one with a Teensy 2 or 3 and a 8-SOIC chip-clip. It can read/write the entire multi-megabit ROM in a minute. Read on for more info...
Software
Mac SE Easter Egg
 |
 |
Using my PROMdate generic EPROM reader, I extracted the Mac SE boot ROMs from a machine I found on the side of the road. We then reverse engineered the easter egg photographs of the development team hidden in the extra space. Read on for more details...